After about 60 days using my MacBook Pro running Mac OS X Lion (10.7.3), I saw some sluggishness in some apps. At first, it was Messages (iChat replacement for Mountain Lion). It went unresponsive and displays the rainbow wheel for a few seconds, enough to annoy an impatient user.
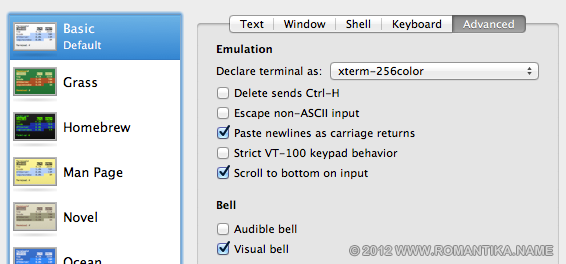
Then, the same behavior happened in Terminal. This is where I realize the common behavior. You know, when you press delete on an empty prompt, you get a bell. The default is the audible bell. When I change it to the visual bell, sluggishness disappeared.
On Messages, I had the default sound effect setting when messages are received or sent.
Boy was I right. In the log /var/log/system.log there were a bunch of these:
May 3 22:30:57 ADYMAC iChat[66352]: [Warning] Actions: Couldn't create SystemSound from /Applications/iChat.app/Contents/Resources/Received Message.aiff
May 3 22:31:07 ADYMAC iChat[66352]: [Warning] Unable to find a sound action ID for /Applications/iChat.app/Contents/Resources/Received Message.aiff errorResult: 268435460
May 3 22:31:07 ADYMAC iChat[66352]: [Warning] Actions: Couldn't create SystemSound from /Applications/iChat.app/Contents/Resources/Received Message.aiff
May 3 22:31:17 ADYMAC iChat[66352]: [Warning] Unable to find a sound action ID for /Applications/iChat.app/Contents/Resources/Received Message.aiff errorResult: 268435460 |
May 3 22:30:57 ADYMAC iChat[66352]: [Warning] Actions: Couldn't create SystemSound from /Applications/iChat.app/Contents/Resources/Received Message.aiff
May 3 22:31:07 ADYMAC iChat[66352]: [Warning] Unable to find a sound action ID for /Applications/iChat.app/Contents/Resources/Received Message.aiff errorResult: 268435460
May 3 22:31:07 ADYMAC iChat[66352]: [Warning] Actions: Couldn't create SystemSound from /Applications/iChat.app/Contents/Resources/Received Message.aiff
May 3 22:31:17 ADYMAC iChat[66352]: [Warning] Unable to find a sound action ID for /Applications/iChat.app/Contents/Resources/Received Message.aiff errorResult: 268435460
These are when I tried to change the system bell using the System Preferences application.
May 11 01:45:55 adymac System Preferences[44495]: Error 268435460 setting AlertSound
May 11 01:53:22 adymac System Preferences[44678]: Error 268435460 setting AlertSound
May 11 01:58:20 adymac System Preferences[44678]: Error 268435460 setting AlertSound
May 11 01:58:25 adymac System Preferences[44678]: Error 268435460 setting AlertSound |
May 11 01:45:55 adymac System Preferences[44495]: Error 268435460 setting AlertSound
May 11 01:53:22 adymac System Preferences[44678]: Error 268435460 setting AlertSound
May 11 01:58:20 adymac System Preferences[44678]: Error 268435460 setting AlertSound
May 11 01:58:25 adymac System Preferences[44678]: Error 268435460 setting AlertSound
And so I tried a lot of things, including logging out then in, inspecting the file permissions, and also ran the verify permission utility on the hard disk using Disk Utility. Nothing worked.
Finally, I saw that there was one process called coreaudiod
_coreaudiod 45197 0.0 0.1 2453172 5228 ?? Ss Fri02AM 0:10.52 /usr/sbin/coreaudiod |
_coreaudiod 45197 0.0 0.1 2453172 5228 ?? Ss Fri02AM 0:10.52 /usr/sbin/coreaudiod
And so I tried killing it:
$ sudo killall coreaudiod |
$ sudo killall coreaudiod
And as expected, it respawned itself and all audio effects were now working. Sluggishness and the dreaded rainbow wheel are gone.
Googling after, I saw that people mentioned that this may be a bug, and killing coreaudiod is only a workaround not the solution.
Come to think of it, it also caused unnecessary delay when making screen shots using the Command-Shift-4 key combination.
I hope this can save you some time.