Today, I saw that Facebook introduced some new features, and one intriguing feature is called “Facebook Social Plugin“. It would be very interesting to have blog posts to be simply “liked”, and having information displayed about activities and recommendations related to your website.
So I decided to take 30 minutes of my break time and write this simple plugin. Since I don’t have much time I decided not to explore XFBML and the SDK as yet. That is why it’s called BASIC. With XFBML, shorter codes can be used, and deeper integration between Facebook and your website can be achieved. I am intrigued, really but I must be realistic.
This plugin is a very simple plugin to embed :
- “like” button at the end of your articles/blog posts
- activity feed as a widget
- recommendations as a widget
- Like box as a widget
You can add these cool features with minimal effort.
Most configuration parameters are self-explanatory, but Domain Override simply means you want to display information about another domain instead of where the widgets are hosted. By the way, the widget settings are combined in the Settings > Basic Facebook Social Plugins page.
At this moment this plugin is still waiting to be hosted at the official WordPress Plugin Directory so it can only be downloaded here.
Basic Facebook Social Plugins Version 1.0Basic Facebook Social Plugins Version 1.1* This version will wipe out previous widget settings as it introduces multiple instances of widgets.Basic Facebook Social Plugins Version 1.2
Once available there, a link will be provided. When it’s there, It’s now in the official plugin directory (basic-facebook-social-plugins) so you should be able to install it using the automated, built-in plugin installer too.
You can see the sample for the like button at the end of this post, and the widgets live on this site.
The widgets does not conform to your theme (does not inherit your theme css) but simply bare boxes with Facebook feel. Take note that styling inside the boxes (and texts) are provided by facebook.
Those of you who are concerned about privacy, you’ll be glad to know that your name and profile picture will not just be displayed to anyone:
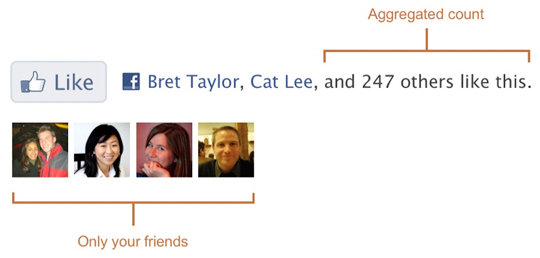
(This also applies to recommendation and activity box. Only friends will be able to see that you like something.) Facebook has thought of everything.
Try it out and let me know how it works for you.
Shots from Facebook:
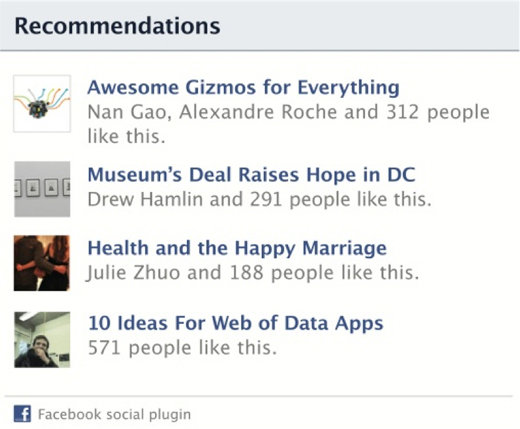
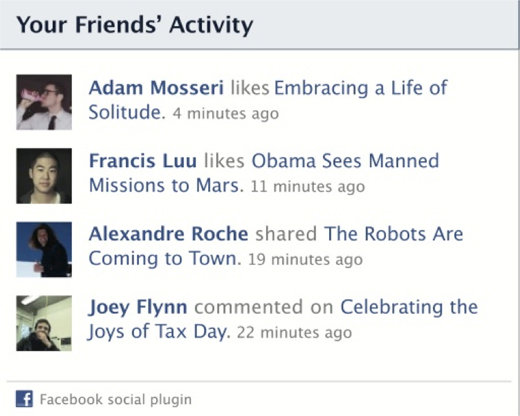
Facebook has also written a nice post about social plugins in their blog: Answers to Your Questions on Personalized Web Tools.
Note:
- This WordPress plugin is written entirely by me, and is provided as-is with no guarantee. It is neither approved nor endorsed by Facebook.
- Yes, it is breakable by Facebook if they decide to change the iframe URL.