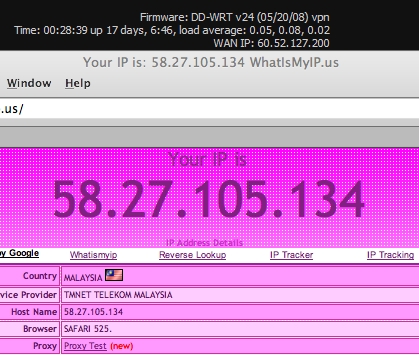
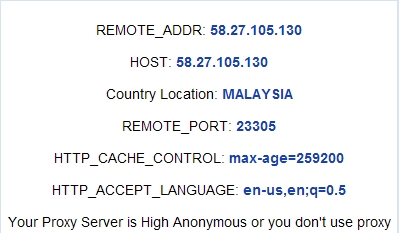
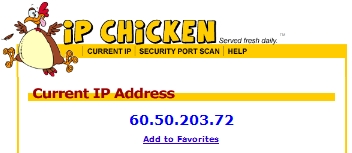
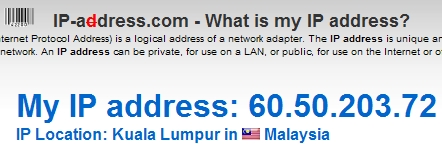
I was going after a moron who was disturbing my wife’s blog and reached an IP number. Utilizing nmap, I found out that port 80 on the IP is open.
-(~:#)-> nmap -A -T4 XXX.XXX.XXX.XXX Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2009-02-09 23:52 MYT Warning: Giving up on port early because retransmission cap hit. WARNING: RST from port 80 -- is this port really open? WARNING: RST from port 80 -- is this port really open? WARNING: RST from port 80 -- is this port really open? WARNING: RST from port 80 -- is this port really open? Insufficient responses for TCP sequencing (0), OS detection may be less accurate Interesting ports on XXX.XXX.in-addr.arpa (XXX.XXX.XXX.XXX): Not shown: 1673 closed ports PORT STATE SERVICE VERSION 25/tcp filtered smtp 80/tcp open http (GoAhead-Webs embedded httpd) 443/tcp open ssl/unknown 1720/tcp filtered H.323/Q.931 5000/tcp open UPnP? 5001/tcp open commplex-link? 5100/tcp open admd? 1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at http://www.insecure.org/cgi-bin/servicefp-submit.cgi : SF-Port443-TCP:V=4.11%T=SSL%I=7%D=2/9%Time=499051AA%P=i686-pc-linux-gnu%r( SF:GetRequest,18A,"HTTP/1\.0\x20501\x20Not\x20Implemented\r\nContent-type: SF:\x20text/html\r\nPragma:\x20no-cache\r\nDate:\x20Mon,\x2009\x20Feb\x202 SF:009\x2015:54:17\x20GMT\r\nLast-modified:\x20Mon,\x2009\x20Feb\x202009\x SF:2015:54:17\x20GMT\r\nAccept-Ranges:\x20bytes\r\nConnection:\x20close\r\ SF:n\r\n\r\n<html>\n<head>\n\x20\x20<title>501\x20Not\x20Implemented\n</title></head>\n<body \x20bgcolor=\"ffffff\">\n\x20\x20<h2>501\x20Not\x20Im SF:plemented</h2><h2>\n\x20\x20<p>\n\x20\x20The\x20requested\x20method\x20is\x2 SF:0not\x20implemented\x20by\x20this\x20server\.\n</p></h2></body>\n</html>\n")%r(G SF:enericLines,18A,"HTTP/1\.0\x20400\x20Bad\x20Request\r\nContent-type:\x2 SF:0text/html\r\nPragma:\x20no-cache\r\nDate:\x20Mon,\x2009\x20Feb\x202009 SF:\x2015:54:17\x20GMT\r\nLast-modified:\x20Mon,\x2009\x20Feb\x202009\x201 SF:5:54:17\x20GMT\r\nAccept-Ranges:\x20bytes\r\nConnection:\x20close\r\n\r SF:\n\r\n<html>\n<head>\n\x20\x20<title>400\x20Bad\x20Request</title>\n\n<body \x20bgcolor=\"ffffff\">\n\x20\x20<h2>400\x20Bad\x20Request<h SF:2>\n\x20\x20<p>\n\x20\x20Your\x20request\x20has\x20bad\x20syntax\x20or\ SF:x20is\x20inherently\x20impossible\x20to\x20satisfy\.\n</p></h></h2></body>\n</head></html>\ SF:n")%r(HTTPOptions,18A,"HTTP/1\.0\x20501\x20Not\x20Implemented\r\nConten SF:t-type:\x20text/html\r\nPragma:\x20no-cache\r\nDate:\x20Mon,\x2009\x20F SF:eb\x202009\x2015:54:18\x20GMT\r\nLast-modified:\x20Mon,\x2009\x20Feb\x2 SF:02009\x2015:54:18\x20GMT\r\nAccept-Ranges:\x20bytes\r\nConnection:\x20c SF:lose\r\n\r\n\r\n<html>\n<head>\n\x20\x20<title>501\x20Not\x20Implemente SF:d</title>\n</head>\n<body \x20bgcolor=\"ffffff\">\n\x20\x20<h2>501\x20No SF:t\x20Implemented</h2><h2>\n\x20\x20<p>\n\x20\x20The\x20requested\x20method\x SF:20is\x20not\x20implemented\x20by\x20this\x20server\.\n</p></h2></body>\n</html>\ SF:n")%r(RTSPRequest,18A,"HTTP/1\.1\x20501\x20Not\x20Implemented\r\nConten SF:t-type:\x20text/html\r\nPragma:\x20no-cache\r\nDate:\x20Mon,\x2009\x20F SF:eb\x202009\x2015:54:18\x20GMT\r\nLast-modified:\x20Mon,\x2009\x20Feb\x2 SF:02009\x2015:54:18\x20GMT\r\nAccept-Ranges:\x20bytes\r\nConnection:\x20c SF:lose\r\n\r\n\r\n<html>\n<head>\n\x20\x20<title>501\x20Not\x20Implemente SF:d</title>\n</head>\n<body \x20bgcolor=\"ffffff\">\n\x20\x20<h2>501\x20No SF:t\x20Implemented</h2><h2>\n\x20\x20<p>\n\x20\x20The\x20requested\x20method\x SF:20is\x20not\x20implemented\x20by\x20this\x20server\.\n</p></h2></body>\n</html>\ SF:n"); Device type: general purpose Running: Microsoft Windows Longhorn OS details: Microsoft Windows Longhorn Preview Nmap finished: 1 IP address (1 host up) scanned in 122.444 seconds |
And so I went to look at what the HTTP server offers. It’s a D-Link DCS-950 camera, most probably port-forwarded using a router since the browsing IP from the computers are also the same.
I went to the D-Link website to look for the product manual and as I suspected it is using the default password, admin/admin. Here’s what i saw:
[singlepic=21,600,600]
Anyone recognize this place?
The point here is that a device that is intended to serve as a security tool, can also be used against you. The dumbest thing you can do it leaving your devices on default passwords.
Ha… I can see someone changing tab to open their router configuration panel which have the default password. 😉
But hey, this camera is cool. I would not hesitate to install one or two at home. It can also be a PPPoE dialer (ADSL) so it can connect directly to a modem and dial the Internet. One bad thing I noticed is that to login and browse the images you need to use IE as it utilizes ActiveX.