In my previous post about passwords, I wrote about why you should not use shared passwords. One thing after another, in the comments section password storage became a topic and I suggested KeePass and at all cost avoid online password managers. I had a reason in mind, and you have guessed it right – security.
While it is possible to have a secure online password manager, it is not possible to see any source code for such system if it is implemented using server-side programming (processing done on server, e.g. PHP). Why see the source code? Well, that is the base of all security system – so that people who knows how to read the source code to figure out what a particular piece of software does, and if it is really secure and contains no malicious code.
As a matter of fact, someone just told me that I should include the source code of the Portable Pidgin I packaged so that he can be sure that I didn’t put anything malicious in there. I did, and the source has always been there since the very beginning.
Back to online password storage, one of the guys at Clipperz contacted me and asked me to look closely at the system and to analyze the source code of the JavaScript. And I did just that. I am not going into detail on what features Clipperz have, as you can always read it on their site. I am going to focus on the security side, while trying to stay as not technical as possible.
Please click on Continue Reading if you are interested to read the rest of the article.
Source Code
I am neither a math nor crypto expert, but as a programmer the source code make sense to me. The implementation is beyond my wildest imagination. The next statement will make me look dumb, but honestly I have never thought that encryption is possible with client-side scripts (processing done on local machine, e.g. JavaScripts). This is especially more difficult due to the way different browsers interpret such scripts.
When you first access Clipperz, the JavaScript source code are downloaded and executed on your local machine. For users with slower processing power (like my Pentium III 600MHz) you will notice a slowdown when your machine struggles to execute the JavaScripts.
You can say that, your machine has become the server and process everything for you. When you create your “account” in Clipperz, they don’t even ask for an email address. As a matter of fact it is not a real account – your PC creates all data in encrypted chunks and send it to the server using your username as reference.
Your data is encrypted using a key – this is simply your password which is not stored anywhere unless you write is somewhere. The same key is used to decrypt the data, that is to convert the gibberish text to something that can be read and have a meaning. It is a straight-forward process.
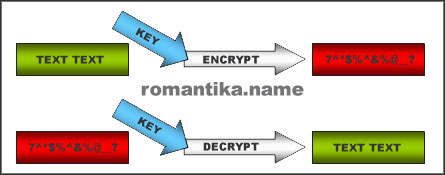
So be really really careful not to lose your password or you’ll lose data.
Network Traffic
I captured my network traffic while using Clipperz with Wireshark, and of course tcpflow on Linux. However due to the connection being established in HTTPS, the streams between the server and the browser is already encrypted and all I see is gibberish. This means that I am unable to confirm whether or not the application actually sends encrypted data at the server end.
The true intention of the network traffic capture is the time line. I was able to see that as I used the application inside the browser, no communication was made. This confirms that all processing is actually done on the browser side. Only when I clicked save, data communication occurs between the browser and the server.
Because of this, it is not very helpful to include a screenshot here, unless a video is made.
User Interface
As mentioned earlier, when not sending or receiving data from the server the application is actually running in your browser. Because of this requirements, Clipperz utilizes YUI which provides interactive and rich application. It’s a great library, I use it in some of my projects too.
Conclusion
I am stubborn and most importantly very paranoid when it comes to security. I will still not use any online password managers for my extremely confidential accounts, no matter how good they are. I must admit though, that Clipperz certainly has changed my view on online password managers, and I am planning to use it for my many online accounts (since I don’t use shared passwords, remember? 😉 ).
Another reason why I trust Clipperz is that they have released the crypto library for everyone to use: Clipperz crypto library hosted on Google Code.
Also, I have so many system passwords such as OS logins, database logins, etc. to development servers I sometimes have to log in to them without being connected to the Internet. This is a concern with online password managers, but not with Clipperz as there exist an offline version.
It might also be useful to know that Clipperz have a compact version to be used as Firefox sidebar. This is particularly useful for direct logins that you have configured.
Well done Marco and Giulio for such a wonderful project.
This post is not sponsored. It is purely based on my opinion.



If you are interested on what data the Clipperz application is sending/receiving from the server, I suggest to use FireFox with the FireBug extension.
FireBug allows to log to the console all the XHR requests, so you can inspect all the details of the communication protocol.
Try PassPack when you have the time. It’s another awesome online password manager. I have a small review on my blog you could get more info from.
http://thedaneshproject.com/internet/my-password-manager/
@Giulio: Ah yes I totally forgot about that. Shall try it soon.
@danny: Thanks. I shall look at it once I find the time.